Docker是一个开源的应用容器引擎,本身功能已经逐步满足我们日常要求,但是一直对管理Docker容器之间的交互和跨主机集群的网络配置一直空缺,需要依赖外部工具来实现。最近看了一篇infoQ的文章:5个解决Docker网络问题的项目,概述了目前主流的五个工具:Weave、Kubernetes、CoreOS, Flannel、Pipework以及SocketPlane。其中Weave是由Zett.io公司开发的,它能够创建一个虚拟网络,用于连接部署在多台主机上的Docker容器,这样容器就像被接入了同一个网络交换机,那些使用网络的应用程序不必去配置端口映射和链接等信息。外部设备能够访问Weave网络上的应用程序容器所提供的服务,同时已有的内部系统也能够暴露到应用程序容器上。Weave能够穿透防火墙并运行在部分连接的网络上,另外,Weave的通信支持加密,所以用户可以从一个不受信任的网络连接到主机。下面我们实际来试一试吧。
首先要确保Linux(内核3.5之上版本),并安装了Docker(0.9.1之上)。下面的测试基于Ubuntu 14.04LTS(3.13.x)和Docker 1.5。然后直接通过下面的方式直接下载二进制文件安装:
|
1 2 3 4 5 6 7 |
sudo wget -O /usr/local/bin/weave \ https://github.com/zettio/weave/releases/download/latest_release/weave sudo chmod a+x /usr/local/bin/weave weave version weave script 0.9.0 weave route 0.9.0 ...... |
接下来运行weave launch,这条命令是在容器中运行一个weave router,需要在每台主机上都启用这个服务。该服务所需的docker镜像weavetools会自动下载。另外,执行weave launch之前要保证有bridge-utils网桥工具包。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
# apt-get install bridge-utils # weave launch Unable to find image 'zettio/weavetools:0.9.0' locally Pulling repository zettio/weavetools 6c2dd751b59c: Pulling image (0.9.0) from zettio/weavetools 6c2dd751b59c: Pulling image (0.9.0) from zettio/weavetools, endpoint: https://registry-1.docker.io/v1/ ...... Status: Downloaded newer image for zettio/weavetools:0.9.0 034aa3cdd9a7f2595f15e08de8b9644f726cc577c6544ee668207557f4a9bccc # 通过brctl show,可以看出weave新创建了一个网桥。 # brctl show bridge name bridge id STP enabled interfaces docker0 8000.56847afe9799 no veth5bb9b18 weave 8000.7af757d87fdc no vethwepl3537 |
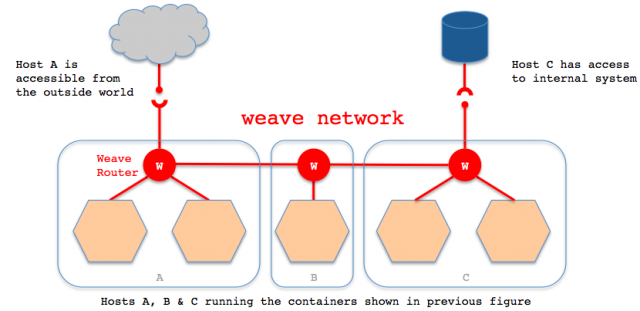
所有容器的网络通讯都通过route服务和网桥转发。如下图所示:
在第一台主机test01上运行:
|
1 |
weave launch |
然后再第二台主机test02上运行,
weave launch 192.168.1.201
这个命令相当于在本地启动了weave route,再通过weave connect 192.168.1.201来和192.168.1.201的route容器建立连接。这样weave route就能相互能找到remote主机。我在这里遇到一个天坑:一定注意不要使用主机名,哪怕在/etc/hosts文件中的。weave会通过DNS主机(202.106.195.68)来定位这台主机了,等待很久后出现超时:invalid peer address: lookup test03 on 202.106.195.68:53: read udp 202.106.195.68:53: i/o timeout.
这时候通过docker logs -f来查看route容器的日志,可以看出route已经找到对端的MAC地址。如果不通,可以检查了本地6783端口的监听和防火墙是否有问题。
|
1 2 |
weave 2015/02/13 15:58:40.019973 Discovered remote MAC 7a:56:0e:02:ed:3c at 7a:56:0e:02:ed:3c ...... |
OK! 接下来运行应用的容器。我们需要给出IP地址和网段,以CIDR(无类别域间路由,IP地址+掩码)的形式。weave run命令会调用docker run -d(同理,weave start会调用docker start)以及下面的IP地址和网络的形式。所以我们可以用这种方式运行任意容器。如果我们的应用包含了一个以上主机上的容器。我们需要运行下面第二行语句,IP地址和掩码可以是你希望的地址,但要确保他们不会和主机上使用的IP、外部服务的IP以及你想要连接的其他容器的IP地址冲突。官方提供了一个简单的测试容器:errordeveloper/hello-weave启动了一个简单的http服务,而errordeveloper/curl是一个包含curl工具的客户端,
在第一台主机test01上运行:
|
1 2 3 |
C=`weave run 10.0.0.1/24 errordeveloper/hello-weave` docker logs -f $C * Running on http://0.0.0.0:5000/ |
然后在test02上运行:
|
1 2 3 4 5 6 7 8 9 10 11 |
C=`weave run 10.0.0.2/24 -it errordeveloper/curl` docker attach $C / # ping 10.0.0.1 PING 10.0.0.1 (10.0.0.1): 56 data bytes 64 bytes from 10.0.0.1: seq=0 ttl=64 time=5.853 ms 64 bytes from 10.0.0.1: seq=1 ttl=64 time=4.860 ms ...... # 下面我们测试一下curl / # curl 10.0.0.1:5000 Hello, Weave! # 连接成功! |
关于weave原理的描述:
Weave creates a network bridge on the host. Each container is connected to that bridge via a veth pair, the container side of which is given the IP address & netmask supplied in ‘weave run’. Also connected to the bridge is the weave router container.
A weave router captures Ethernet packets from its bridge-connected interface in promiscuous mode, using ‘pcap’. This typically excludes traffic between local containers, and between the host and local containers, all of which is routed straight over the bridge by the kernel. Captured packets are forwarded over UDP to weave router peers running on other hosts. On receipt of such a packet, a router injects the packet on its bridge interface using ‘pcap’ and/or forwards the packet to peers.
Weave routers learn which peer host a particular MAC address resides on. They combine this knowledge with topology information in order to make routing decisions and thus avoid forwarding every packet to every peer. The topology information captures which peers are connected to which other peers; weave can route packets in partially connected networks with changing topology.
Weave routers establish TCP connections to each other, over which they perform a protocol handshake and subsequently exchange topology information. These connections are encrypted if so configured. Peers also establish UDP “connections”, possibly encrypted, for the aforementioned packet forwarding. These “connections” are duplex and can traverse firewalls.
^^

docker
Pingback: Docker学习笔记 — Weave实现跨主机容器互联-鲸鱼云
打开 288d.pw 都是 浪美眉
这爱莎是马云家的吧?
存在的不一定是正确的。不要偷换概念……小偷强盗也是存在的,还不能全盘否定?